Network Security
- Towards Protection, Detection, and Recovery from Windows-based Crypto Ransomware
Faculty Lead: Ambareen Siraj, Student: Md. Ahsan Ayub
Ransomware is a special type of malware that seizes control over a computing system, encrypts valuable and critical assets, and demands ransom to return back the control to the owner. According to the recent cyber threat reports, recovery from the devastating ransomware attacks takes on average 16 days, and its global damage is predicted to reach US$ 20 billion by 2021. Due to the severity of the aftermath of such extortion-based cyber-attacks, we take on confronting this ever-evolving challenge on protection against, detection of, and recovery from ransomware through static and dynamic analysis. To begin our analysis, we performed a data-driven study, presenting early ransomware detection approaches with the help of sequence mining and machine learning techniques. We select I/O Request Packet (IRP), a low-level file system logs, in order to gain actionable, granular insights on ransomware encryption processes, extract distinguishable sequential operations carried out by ransomware during its execution, and perform prediction on all the studied ransomware families, an application of multiclass classification. To protect us from ransomware, we leverage static analysis tools to gain useful knowledge on how the authors built the malicious samples / programs; followed by, employ machine and deep learning algorithms to learn its underlying pattern. Our future goal includes exploring unique ways to create copies of the files before they are encrypted by the ransomware process(es) with an emphasis on obtaining less memory overhead as well as faster computation.
- Model Evasion Attack on Intrusion Detection Systems using Adversarial Machine Learning
Faculty Lead: Douglas A. Talbert and Ambareen Siraj, Students: Md. Ahsan Ayub and William A. Johnson
Intrusion Detection Systems (IDS) have a long history as an effective network defensive mechanism. The systems alert defenders of suspicious and / or malicious behavior detected on the network. With technological advances in AI over the past decade, machine learning (ML) has been assisting IDS to improve accuracy, perform better analysis, and discover variations of existing or new attacks. However, applications of ML algorithms have some reported weaknesses, and, in this research, we demonstrate how one of such weaknesses can be exploited against the workings of the IDS. The work presented in this work is twofold: (1) we develop a ML approach for intrusion detection using Multilayer Perceptron (MLP) network and demonstrate the effectiveness of our model with two different network-based IDS datasets; and (2) we perform a model evasion attack against the built MLP network for IDS using an adversarial machine learning technique known as the Jacobian-based Saliency Map Attack (JSMA) method. Our experimental results show that the model evasion attack is capable of significantly reducing the accuracy of the IDS, i.e., detecting malicious traffic as benign. Our findings support that neural network-based IDS is susceptible to model evasion attack, and attackers can essentially use this technique to evade intrusion detection systems effectively.
- A Protoco Independent Approach in Network Covert Channel Detection
Faculty Lead: Ambareen Siraj, Students: Md. Ahsan Ayub and Steven Smith
Network covert channels are used in various cyber-attacks, including disclosure of sensitive information and enabling stealth tunnels for botnet commands. With time and technology, covert channels are becoming more prevalent, complex, and difficult to detect. The current methods for detection are protocol and pattern specific. This requires the investment of significant time and resources into application of various techniques to catch the different types of covert channels. This paper reviews several patterns of network storage covert channels, describes generation of network traffic dataset with covert channels, and proposes a generic, protocol-independent approach for the detection of network storage covert channels using a supervised machine learning technique. The implementation of the proposed generic detection model can lead to a reduction of necessary techniques to prevent covert channel communication in network traffic. The datasets we have generated for experimentation represent storage covert channels in the IP, TCP, and DNS protocols and are available upon request for future research in this area.
- Detecting Domain Generating Algorithm Based Malicious Domains using Bigram and Word2Vec
Model
Faculty Lead: Ambareen Siraj, Students: Md. Ahsan Ayub and Steven Smith
Domain Generating Algorithms (DGAs) are used to facilitate covert server communication for carrying out various types of cyber-attacks with botnets. Attackers use these algorithms to evade defensive methods of blocking malicious communication such as blacklisting. Using DGAs, attacks can be facilitated without the fear of command and control (C&C) servers being identified and permanently blocked. Through domain fluxing, attackers making use of DGAs can constantly change the domain used for their C&C server from one to another in short time intervals and anytime they are blocked. Therefore, automated detection of DGA-created domains is a critical countermeasure to prevent malicious botnet communication in a timely manner. In our research, we propose a comprehensive solution to detect malicious DGA-based domains used in malware communication. Two distinct feature extraction methods, the Bigram model and the Word2Vec model, are applied for text processing. Our results demonstrate exceptional success in both binary classifications, classifying a given domain as benign or malicious, and multiclass classification, identifying the specific malware family that produced the domain.
- Data Protection and Access Control in Wireless Sensor Networks
Faculty Lead: Dr. Denis Ulybyshev, in collaboration with Dr. Charles Van Neste (ECE). Students: Trey Burks, Bradley Northern, Vadim Kholodilo
The project focuses on developing the techniques to protect data in wireless sensor networks in transit and at rest. Lightweight encryption schemes are applied on computationally limited devices, such as ESP32 boards, which should be located as close to sensors as possible in the network. Secure OPC servers provide data interoperability and make data export and integration with existing Supervisory Control and Data Acquisition (SCADA) systems easier. SCADA servers are used for data visualization and archiving. A secure mechanism to provide sensor data export to authorized external third parties is being developed. Our methodology integrates with Relational Database Management Systems (RDBMS) and provides fine-grained role-based and attribute-based access control, data confidentiality and integrity, as well as data origin integrity.
- Secure and Privacy Preserving Traffic Management Schemes for VANETs
Significant time and gas are wasted every day as a result of traffic congestion and slow traffic. The high economic loss is not the only harmful consequence. The air pollution resulted from wasted fuel and carbon dioxide emissions causes a lot of serious health and environment problems. Unfortunately, with the unbalanced ratio of the new constructed roads and the number of new vehicles, the traffic congestion problem is expected to worsen and the impact on citizens will grow as a result. In Vehicular Ad Hoc Networks (VANETs), vehicles are equipped with wireless communication capabilities and collaboratively form a network in an ad hoc manner. VANETs can play a great role in avoiding these problems by sending guidance to vehicles to pursue alternative routes. Live traffic reports are used to provide continuous updates about the roads congestion status. The majority of these reports are based on the current traffic situations and cannot predict the future conditions of the road. However, these applications would not help drivers who are already stuck in congestion because they may not be able to find alternative routes. These reports also may not be able to mitigate slow traffic because they usually warn vehicles after the congestion takes place. Therefore, recent research has focused on avoiding the occurrence of traffic buildup as a better means for decreasing travel time and the amount of carbon dioxide emissions. However, this approach requires each driver to report his/here route. Knowing the future locations of vehicles can be misused by attackers to not only violate people’s privacy but also can be used for physical attacks and robbery.
We have proposed a privacy-preserving route reporting scheme for traffic
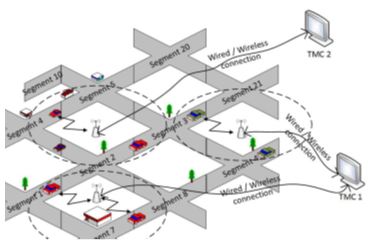 management in VANET. Vehicles provide encrypted segment-based route information to
road side units (RSUs). Instead of sending one message for each route segment, all
the segments’ data can be collected by one message using homomorphic encryption. RSUs
compute the encryption of the expected number of vehicles in each segment of the road
without knowing the actual routes of vehicles. Each RSU shares the vehicles’ routes
information with a traffic management center (TMC), which decrypts the expected total
number of vehicles at different segments of the road without knowing the individual
vehicles’ routes. Then, it conducts analysis and sends predictions and recommendations
back to the RSUs. Passing vehicles solicit hints from RSUs on the expected traffic
condition in order to decide to take an alternating route if there is a potential
of congestion or slow traffic in its main route.
management in VANET. Vehicles provide encrypted segment-based route information to
road side units (RSUs). Instead of sending one message for each route segment, all
the segments’ data can be collected by one message using homomorphic encryption. RSUs
compute the encryption of the expected number of vehicles in each segment of the road
without knowing the actual routes of vehicles. Each RSU shares the vehicles’ routes
information with a traffic management center (TMC), which decrypts the expected total
number of vehicles at different segments of the road without knowing the individual
vehicles’ routes. Then, it conducts analysis and sends predictions and recommendations
back to the RSUs. Passing vehicles solicit hints from RSUs on the expected traffic
condition in order to decide to take an alternating route if there is a potential
of congestion or slow traffic in its main route.The traffic management schemes need the correct number of vehicles in each road segment to calculate correct predictions. However, an individual attacker may launch a Sybil attack by pretending to be multiple simultaneous vehicles to
 compromise the traffic management. In order to preserve the privacy of vehicles, each
vehicle is loaded with several valid pseudonyms and each pseudonym is used for a short
time. However, the abundance of valid pseudonyms can be misused to launch Sybil attack
by correctly authenticating non-existent vehicles. RSUWe first proposed an efficient
pseudonym generation technique. Instead of using asymmetric key cryptography, we use
symmetric key cryptography to decrease the computation overhead. Vehicles receive
a small set of long-term secrets to compute a large number of pseudonyms and keys.
The computations of the pseudonyms by vehicles can significantly decrease the overhead
of frequently contacting a trusted party to send pseudonyms and storing them. The
low overhead of computing pseudonyms can also help boost the privacy efficiently by
using each pseudonym for a short time. We have studied a strong and more realistic
adversary model assuming that attackers can share their pool of pseudonyms to launch
colluding Sybil attacks. We proposed a cross-layer scheme to enable the RSUs to identify
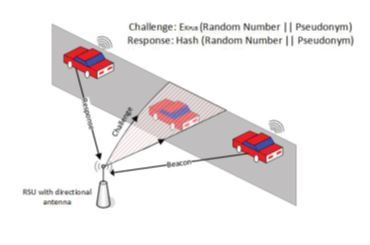
such Sybil vehicles. Since Sybil vehicles do not exist in their claimed locations,
our scheme is based on verifying the vehicles’ locations. A challenge packet is sent
to the vehicle’s claimed location using a directional antenna with beamforming technique
to detect the presence of a vehicle. If the vehicle is at the claimed location, it
should be able to receive the challenge and send back a valid response packet. The
cross-layer design is performed by composing the challenge packet at the MAC layer
and directing the PHY layer to send it to the claimed location. Hash function and
public key cryptography are used to secure the challenge and response packets. In
order to reduce the overhead, instead of sending challenge packets to all the vehicles
all the time, packets are sent only when there is a suspicion of Sybil attack.
compromise the traffic management. In order to preserve the privacy of vehicles, each
vehicle is loaded with several valid pseudonyms and each pseudonym is used for a short
time. However, the abundance of valid pseudonyms can be misused to launch Sybil attack
by correctly authenticating non-existent vehicles. RSUWe first proposed an efficient
pseudonym generation technique. Instead of using asymmetric key cryptography, we use
symmetric key cryptography to decrease the computation overhead. Vehicles receive
a small set of long-term secrets to compute a large number of pseudonyms and keys.
The computations of the pseudonyms by vehicles can significantly decrease the overhead
of frequently contacting a trusted party to send pseudonyms and storing them. The
low overhead of computing pseudonyms can also help boost the privacy efficiently by
using each pseudonym for a short time. We have studied a strong and more realistic
adversary model assuming that attackers can share their pool of pseudonyms to launch
colluding Sybil attacks. We proposed a cross-layer scheme to enable the RSUs to identify
such Sybil vehicles. Since Sybil vehicles do not exist in their claimed locations,
our scheme is based on verifying the vehicles’ locations. A challenge packet is sent
to the vehicle’s claimed location using a directional antenna with beamforming technique
to detect the presence of a vehicle. If the vehicle is at the claimed location, it
should be able to receive the challenge and send back a valid response packet. The
cross-layer design is performed by composing the challenge packet at the MAC layer
and directing the PHY layer to send it to the claimed location. Hash function and
public key cryptography are used to secure the challenge and response packets. In
order to reduce the overhead, instead of sending challenge packets to all the vehicles
all the time, packets are sent only when there is a suspicion of Sybil attack.
Find us on Social Media
Contact Us
Cybersecurity Education, Research and Outreach Center
Office Hours: Monday–Friday, 8AM–4:30PM CDT
(931) 372-3519 | ceroc@tntech.edu
Street Address:
Cybersecurity Education, Research and
Outreach Center (CEROC)
Ashraf Islam Engineering Building (AIEB) 238
1021 Stadium Dr.
Cookeville, TN 38501
Mailing Address:
Tennessee Tech University
Cybersecurity Education, Research and
Outreach Center (CEROC)
Campus Box 5134
Cookeville, TN 38505






