Security in Vehicular Ad-Hoc Networks
Secure and Privacy Preserving Traffic Management schemes for VANETs (Lead: Mahmoud)
Significant time and gas are wasted every day as a result of traffic congestion and
slow traffic. The high economic loss is not the only harmful consequence. The air
pollution resulted from wasted fuel and carbon dioxide emissions causes a lot of serious
health and environment problems. Unfortunately, with the unbalanced ratio of the new
constructed roads and the number of new vehicles, the traffic congestion problem is
expected to worsen and the impact on citizens will grow as a result. In Vehicular
Ad Hoc Networks (VANETs), vehicles are equipped with wireless communication capabilities
and collaboratively form a network in an ad hoc manner. VANETs can play a great role
in avoiding these problems by sending guidance to vehicles to pursue alternative routes.
Live traffic reports are used to provide continuous updates about the roads congestion
status. The majority of these reports are based on the current traffic situations
and cannot predict the future conditions of the road. However, these applications
would not help drivers who are already stuck in congestion because they may not be
able to find alternative routes. These reports also may not be able to mitigate slow
traffic because they usually warn vehicles after the congestion takes place. Therefore,
recent research has focused on avoiding the occurrence of traffic buildup as a better
means for decreasing travel time and the amount of carbon dioxide emissions. However,
this approach requires each driver to report his/here route. Knowing the future locations
of vehicles can be misused by attackers to not only violate people’s privacy but also
can be used for physical attacks and robbery.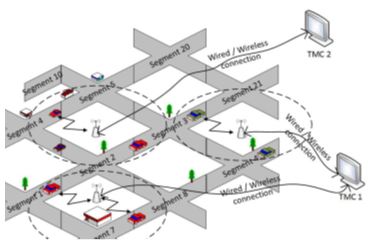
We have proposed a privacy-preserving route reporting scheme for traffic management
in VANET. Vehicles provide encrypted segment-based route information to road side
units (RSUs). Instead of sending one message for each route segment, all the segments’
data can be collected by one message using homomorphic encryption. RSUs compute the
encryption of the expected number of vehicles in each segment of the road without
knowing the actual routes of vehicles. Each RSU shares the vehicles’ routes information
with a traffic management center (TMC), which decrypts the expected total number of
vehicles at different segments of the road without knowing the individual vehicles’
routes. Then, it conducts analysis and sends predictions and recommendations back
to the RSUs. Passing vehicles solicit hints from RSUs on the expected traffic condition
in order to decide to take an alternating route if there is a potential of congestion
or slow traffic in its main route.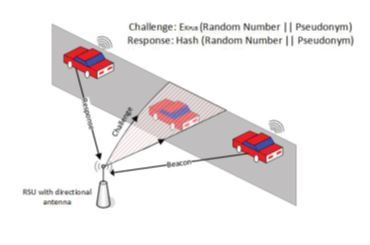
The traffic management schemes need the correct number of vehicles in each road segment to calculate correct predictions. However, an individual attacker may launch a Sybil attack by pretending to be multiple simultaneous vehicles to compromise the traffic management. In order to preserve the privacy of vehicles, each vehicle is loaded with several valid pseudonyms and each pseudonym is used for a short time. However, the abundance of valid pseudonyms can be misused to launch Sybil attack by correctly authenticating non-existent vehicles. RSUWe first proposed an efficient pseudonym generation technique. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the computation overhead. Vehicles receive a small set of long-term secrets to compute a large number of pseudonyms and keys. The computations of the pseudonyms by vehicles can significantly decrease the overhead of frequently contacting a trusted party to send pseudonyms and storing them. The low overhead of computing pseudonyms can also help boost the privacy efficiently by using each pseudonym for a short time. We have studied a strong and more realistic adversary model assuming that attackers can share their pool of pseudonyms to launch colluding Sybil attacks. We proposed a cross-layer scheme to enable the RSUs to identify such Sybil vehicles. Since Sybil vehicles do not exist in their claimed locations, our scheme is based on verifying the vehicles’ locations. A challenge packet is sent to the vehicle’s claimed location using a directional antenna with beamforming technique to detect the presence of a vehicle. If the vehicle is at the claimed location, it should be able to receive the challenge and send back a valid response packet. The cross-layer design is performed by composing the challenge packet at the MAC layer and directing the PHY layer to send it to the claimed location. Hash function and public key cryptography are used to secure the challenge and response packets. In order to reduce the overhead, instead of sending challenge packets to all the vehicles all the time, packets are sent only when there is a suspicion of Sybil attack.
Find us on Social Media
Contact Us
Cybersecurity Education, Research and Outreach Center
Office Hours: Monday–Friday, 8AM–4:30PM CDT
(931) 372-3519 | ceroc@tntech.edu
Street Address:
Cybersecurity Education, Research and
Outreach Center (CEROC)
Ashraf Islam Engineering Building (AIEB) 238
1021 Stadium Dr.
Cookeville, TN 38501
Mailing Address:
Tennessee Tech University
Cybersecurity Education, Research and
Outreach Center (CEROC)
Campus Box 5134
Cookeville, TN 38505






